Image courtesy of York Regional Police
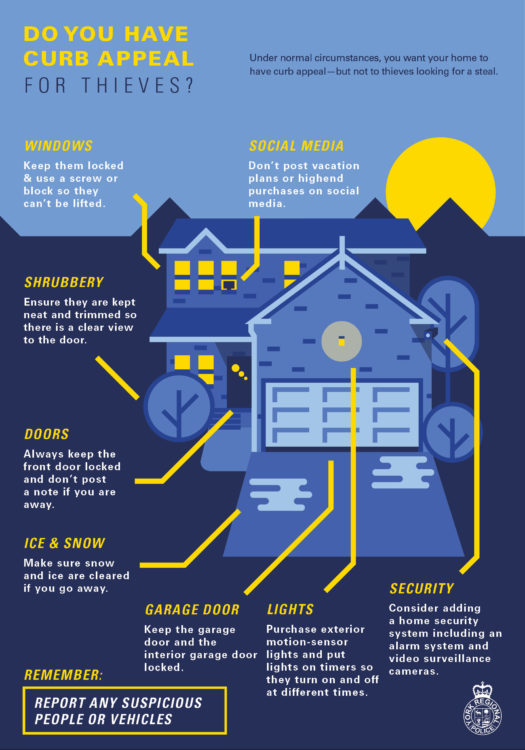
Criminals need victims. By making yourself a harder target, you are limiting their option to choose you. At their core, criminals are lazy (though not always rational). Help ensure they move on to another target. You cannot target proof yourself, but you can harden your target enough that most will pass on by. Put another way, you do not have to outrun the bear, but you do have to outrun someone else.
As always, your mind is your first and best self-defense and safety tool. Start with an adversarial mindset and undertake a vulnerability assessment of your home and its premises. Learn where the weaknesses are and set a plan to mitigate them.
1) Use your locks on windows and doors. Use them all the time. Update the locks (1 inch deadbolts).
This door frame needs pretty much everything, New anchors, plates, jams and locks.
2) Update your door anchors. The door lock is only as good as frame and its anchors.
3) Lock your vehicles and outbuildings. Unlocked doors invite theft.
4) Cameras (external and internal, with recording and some low light capabilities). It is worth noting that cameras are largely post-incident forensic tools. They do have some prevention value though.
5) Good exterior lighting (incl motion sensors). Try not to leave dark corners or avenues of approach.
The bottom lights should be updated with motion sensors like the top.
6) Driveway alarms to let you know when someone has entered the drive.
7) Trim back greenery from the house – eliminate hiding places and or easy points of ingress. CPTED for homes (Crime Prevention through Environmental Design) is a whole other subject worth considering.
This homeowner has work to do. Multiple windows are concealed by greenery.
8) Install an alarm system. Lots of companies can do this, but DIY systems have gotten significantly more robust and easier for non-technical folks to install.
9) Secure your network. Use good password discipline on all your devices. Do NOT use the default passwords that come with your network devices. Keep devices updated and patched as new vulnerabilities are identified and fixed.
10) Perceptions – get a dog. And if you don’t want/can’t have one, build the appearance that you do.
Again, you cannot remove all risk of being targeted. But by assessing your vulnerabilities, and actively working to mitigate them, you can reduce the likelihood of being targeted.
*The views and opinions expressed on this website are solely those of the original authors and contributors. These views and opinions do not necessarily represent those of Spotter Up Magazine, the administrative staff, and/or any/all contributors to this site.