“Whoever can deliver their message without getting caught has the upper hand – NSA
The concept of covert and clandestine communications has been an essential part of successful combat strategy since the beginning of time. The ability to successfully conceal one’s plans from the enemy and to gain intelligence on the enemy without being detected are absolute requirements for success in battle. Sun Tzu’s “Art of War” emphasizes this in the chapters discussing tactical dispositions and the use of spies.
“Thus, what enables the wise sovereign and the good general to strike and conquer, and achieve things beyond the reach of ordinary men, is FOREKNOWLEDGE.”
“Knowledge of the enemy’s dispositions can only be obtained from other men”
– (Sun Tzu on the Use of Spies)
“Conceal your dispositions, and your condition will remain secret, which leads to victory; show your dispositions, and your condition will become patent, which leads to defeat.”
– (Sun Tzu on Tactical Disposition)
THE AMERICAN REVOLUTION
The American Revolutionary resistance began as a clandestine movement to gain independence from the tyranny and overreach of the British Empire. Early American colonials were prisoners in their own homes; held hostage by royal troops in many cases. British parliament mandated that imperial troops be quartered in the homes of the colonists at the will of the empire. This made organizing against them a difficult task. There was no privacy amongst the homes of the colonists. In addition, there was no free speech. Any ill spoken word against the empire or occupying forces could lead to serious punishment.
Communications had to be concealed and coded. The need for concealment and ingenuity of the resistance led to great innovations in the field of clandestine communications. John Jay and Arthur Lee developed “Dictionary Codes”. This was a successful method of transmitting unencrypted messages by using an agreed edition of a specific dictionary. The numbers referred to the page and line of the dictionary where the message would be found.
AN EXAMPLE OF DICTIONARY CODE
The resistance cell agreed on (The Eleventh Edition) of Webster’s Dictionary
The Code would be as follows – (201-5)
The receiver of the coded message would then retrieve an Eleventh Edition Webster’s Dictionary. They would turn to page 201. The message would be written on the fifth line down.
Another form of clandestine messaging would be the use of “Masked Letters”. In using a masked letter, the message sender would create a message on one sheet of paper. They would then use the outline of an eye mask to cut into another sheet of paper. The mask cutout is the template to reveal the hidden message. These would be delivered by courier. One courier would deliver the message and another courier would deliver the mask template in which to decode the message. This redundancy assisted in preventing compromise. In the event of compromise the message and key were separate.
THE MASKED LETTER
THE UNDERGROUND RAILROAD
Between 1810 to 1860 over 100,000 slaves escaped slavery into the Union controlled north or into Canada using a clandestine transportation system known as the Underground Railroad. Africans, black American slaves and other resistors would use coded language hidden in songs and in bible scripture to communicate with one another. Terms such as “Conductor, Station, Passenger, Bundles of Wood and Canaan” were used to describe, guides, safehouses, people to be transported, fugitives and other relevant terms.
SUFFRAGE COOKBOOKS
During the late 1800’s leading into the early 20th century the Women’s Suffrage movement was building. Although the idea of women’s voting rights was popular among women, it wasn’t accepted nationally. This led many leaders within the movement to generate pro suffrage media and information through cookbooks. Many women would write and sell these cookbooks to spread the ideas and concepts of women’s voting rights and to also raise money for their cause. This allowed for the uninhibited transfer of information supporting the movement and fundraising all in one. One such popular cookbook was The Woman’s suffrage cookbook written by Hattie Burr (Boston 1886).
THE FRENCH RESISTANCE UNDER NAZI OCCUPATION IN WWII
9 April 1940, Hitler’s National Socialist military occupied Denmark. By 10 May 1940 the Dutch Resistance had risen. A little over a month later Premiere of France Marshal Henri Phillippe Petain negotiated an armistice with the NAZIs. This led to France being divided into two parts. The Atlantic coast and the northern three-fifths of the country were controlled by NAZIs. The remaining portion of the country was controlled by the pro German Vichy regime headed by Marshal Henri Phillippe. Almost immediately the resistance was formed. Many in the resistance quickly assumed positions within the new government to gain access and placement to enemy information and to sabotage the new regime. Others fled the country to Britain.
Initially the resistance was not well organized and were broken down into factions. They went by many names including but not limited to (Maquis, Partisans, The Resistance and the Freedom Fighters). All of these groups remained separate until the allied invasion in 1944. During the initial stand up of the resistance, groups were easily infiltrated and compromised by the NAZI secret police (Gestapo). The compromises led to an immediate need to develop a complex clandestine method of organization and communication.
It was during these days that Socialist and Communist subversive groups extended their vast array of media and member networks to the cause. The French resistance had an ally in these groups in that the NAZIs opposed Communists and Anarchists. The adage, “An enemy of my enemy is my friend” was true to the word in this case. The Communists and Socialists have historically used worker, trade and labor unions to spread communism and conduct subversive activities promoting the communist agenda. In this instance they were used to produce and distribute anti-NAZI publications, newspapers and other propaganda.
As the resistance developed it had indeed developed a vast and complex array for clandestine communications networks. Many accredit this movement in pioneering today’s modern operating model for clandestine cellular networking. The French Resistance is one of the most historically successful examples of insurgent operations. Many of the methods and techniques employed are still taught to today’s unconventional warriors of American Special Operations.
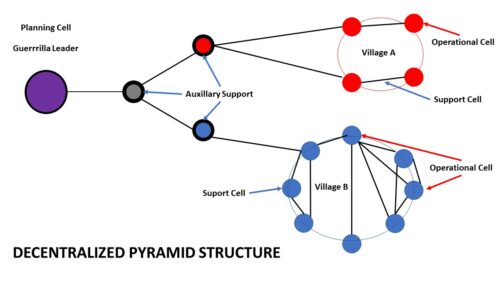
THE PYRAMID STRUCTURE OF COMMAND AND CONTROL
One of the reasons that the resistance was able to remain such an effective threat to the NAZIs was that it was able to remain relatively undetected. Members each had code names. Groups had code names. Each individual and group had encrypted symbols and cryptonyms used to identify them, giving them a degree of anonymity. No member of a partisan group interacted or operated with more than 2 other members of their organization.
No records were kept, and most messages were by word of mouth. If meetings were necessary, they were no larger than a three-person operational group. The three-person model worked efficiently and entailed one person acting as a decoy. One person would transport the weapon or device to execute an attack, act of sabotage or assassination the third person would conduct security and dispose of weapons, equipment or evidence.
This is similar to the model used by insurgents today in Middle East and Central Asian conflicts. One person acquires materials and creates the Improvised Explosive Device. Another person emplaces it, another arms it and yet another to detonate. This decentralized structure allows for a great level of anonymity and doesn’t compromise the resistance leadership. Often times members of the operational cells never meet the person giving the orders.
PYRAMID STRUCTURE
COVERT VS CLANDESTINE
There is a difference in the world of Special Operations. Many people do not understand the difference between the two words “Covert” and “Clandestine”. When an operational cell executes a covert operation, generally the sponsor is concealed. There remains an air or plausible deniability. In clandestine operations the entirety of the operation is hidden. In many cases the operation itself may be concealed from the participants.
SUPPORT AND AUXILIARY SUPPORT
These two terms make up what is known as infrastructure cells. They are separate from the operational cells and are essential in providing the operational cells the support they need to execute operations without being detected. These are some of the services that Support and Auxiliary Support provide the resistance:
- Forgeries
- Documentation
- Currency
- Apartments and Safe houses
- Communications
- Transportation
- Information and intelligence
- Arms
- Training
- Psychological Operations
- Propaganda
- Finance
COMPLEXITY AND REDUNDANCY IN COMMUNICATIONS
Perhaps it was the French Resistance failures that led to one of their greatest successes. In the early days of the resistance the NAZI Gestapo easily infiltrated some of the resistance cells. This in turn led to some of the most horrific reprisals by the NAZIs. In one such instance an entire village was slain. The result of such inhumanity on the part of the NAZIs was the development of a complex communication system with several built-in redundancies.
The resistance used a complex decentralized redundant system for communications. Every member of every cell and every operational group was identified by symbol and cryptonym (Code name). They used a variety of messaging systems from word of mouth in person messages relayed by agents, to concealment devices containing coded messages delivered by courier. Underground newspapers and leaflets were handed out in public with secret messages to the resistance coded in poetry. They even used broadcast radio operated by resistance members outside the country to relay messages to other cells and groups in occupied France.
There are several books written about the resistance in France and their methods and techniques for communication. Raymond and Lucy Aubrac wrote the “French Resistance 1940 – 1944” detailing accounts that took place during the German Occupation of France. Another title explains how the French Resistance had created their own version of the Underground Railroad for downed Allied Airmen. The book “Silent Heroes: Downed Airmen and the French Underground” by Ottis Sherri Greene and the University of Kentucky Press. Yet another title is a great reference on how the resistance utilized women as a resource to fight the NAZIs. Margaret Collins wrote, “Sisters in the Resistance: How Women Fought to Free France 1940 – 1945”.
The result of the advancement in clandestine communications was a drain to the NAZIs and forced them to increase their use of spies. This required the Germans to approach their fight against the insurgency on two fronts. They employed technological means as well as human.
CLANDESTINE COMMUNICATIONS METHODS EMPLOYED BY THE FRENCH RESISTANCE
The resistance understood the value of redundancy in communications and it is for this reason that they ensured messages were often delivered by multiple means to the same person. Redundancy via separate means meant that there was more certainty the message would be delivered and received. It was also less likely to result in a compromise.
WORD OF MOUTH
These messages would be face to face and would require a specified level of verification. A bonifides would be required by both parties. In most cases messages delivered were between two couriers that did not know the recipient and would likely never see them again after the message was delivered. These meetings could be as simple as a “Pass” or a “Brush Pass” where a quick message would be delivered to the recipient or even a short meeting, often disguised as a chance encounter. The bonifides would consist of the following:
Each Party being at the proper location at the right time
Members of the party would wear an agreed upon or designated article of clothing to identify as far recognition (I.E.) One member would be wearing a red beret with tan scarf. The other party would be wearing a black beanie and dark blue denim jacket
A specified hand gesture – The removal of the beret and wiping sweat from one’s brow.
Bonifides challenge and pass, (Challenge) “Excuse me sir, I’m looking for the fabric warehouse on 24th and Westerly.” (Pass) “I believe you’re looking for the seamstress on 25th and Easterly.”
In the above example the courier and the receiver identify each other as the correct person by being at the right location at precisely the right time. In the event that there are several others at the meeting location, additional identifying criteria is required. The courier will be wearing a red beret and a tan scarf. The receiver will be wearing a black beanie and dark blue denim jacket.
Once they have identified one another, the courier will initiate and let the receiver know that it is safe to approach by removing his beret and wiping sweat from his brow. This is when the receiver will initiate the bonifides challenge, “Excuse me sir, I’m looking for the fabric warehouse on 24th and Westerly.” Ideally the courier will respond with the predesignated response, “I believe you’re looking for the seamstress on 25th and Easterly.” If the courier does not give the appropriate response it is likely that the courier is compromised, a threat to compromise has been identified or something has changed last minute, and the meet will not happen at this time.
It is for this reason that many operators and couriers have a secondary meet or even a dead drop pick up planned. In the hypothetical scenario above and the bonifides was not delivered the receive would simply carry on along his predesignated route and on to the next meet or pick up sight. Often an alternate code may be identified notifying the potential receiver that the situation is not safe. A phrase such as, “I’ sorry sir, I cannot help you with directions”. These are called duress codes.
If a meet is scheduled it is often a very short ordeal that takes place either on the move or under the guise of a chance meeting at a public place. These meetings are quick and are extremely cautious as not to draw attention. Duress codes are employed during these meetings to signal to the participants that the meeting needs to be cut immediately or risk compromise. Once the bonifides have been vetted, the messenger is quick to exchange any pertinent information and then both parties move on along the rest of their predesignated route. The exchange is generally described as the “Mad minute” and that is when the 5 W’s are exchanged. The 5 W’s who, what, when, where, why and how. This is also known as the 5W’s and 1 H.
HAND-OFFS AND CONCEALMENT DEVICES
These were executed using the format as word of mouth passes and meetings. Only in these passes the courier is often transporting a small concealment device of some kind containing a message. These can be encrypted or unencrypted. The concealment devices are often very small. They are generally small enough where they can be easily hand carried and passed off undetected. Many are no larger than the size of a penny or a dime.
They are commonly passed off as a handshake or placed in the open where the receiving party can smoothly pick it up. A common depiction of this method is seen in Hollywood spy films where one spy walks up to the other in a crowded airport, brushes by the other and drops something in the other’s coat. Its also depicted as the old briefcase switch.
EXAMPLE OF A CONCEALMENT DEVICE



The above photos depict an example of a bar of soap used as a concealment device containing an encrypted message. In this instance the courier would place the bar of soap with the hidden message at a specific location on the shelf containing the same brand of soap. “Colgate’s Octagon Soap Shelf, First column on the left, three columns back bottom bar of soap. The receiver would then follow the instructions to the tee, pick up the specified bar, purchase it and extrapolate the hidden message
DEAD DROPS
Not all messages were relayed via word of mouth. Although word of mouth is most secure, there are occasions when a meet may not be possible. For dead drops and dead drop boxes, the courier will arrive to the destination where the drop is to occur. He or she will drop the concealment device off at the appropriate location that has already been predesignated and communicated to the receiver. They will then generally move on along their predetermined route undetected.
The receiver will generally arrive after the drop has occurred or has timed it to where they witness the drop occur and them make the pick-up. These drops and pick-ups should occur in a natural manner and should not draw attention. In dead drops the drop site is generally located somewhere easily identifiable near an object that is immovable. These can be executed in rural or urban areas. Dead drops require a greater skill set in execution than word of mouth and must be exact. Concealment devices should be natural and blend in with the environment while at the same time being identifiable by the receiver.
SURVEILLANCE DETECTION ROUTES
Couriers and operatives had to be extremely cautious as to not expose their actions to secret police and other NAZI spies. No-one could be trusted. It is for this reason that members of the resistance were quite paranoid and for good reason. A compromise often led to torture and death. The development of what are known as surveillance detection routes were used. These are routes that occur naturally within one’s everyday life and employ a variety of “Cover Stops” where one can conduct meetings, execute hand-offs, make a dead drop or a pickup. They could also use their cover stops to identify any surveillance that may have been tailing them.
A typical surveillance detection route is specific to each agent and should be a natural part of their everyday life. An example is every Tuesday, Thursday and Saturday, Jean would wake up, go to the local diner for breakfast by foot. Then after breakfast he would take the train to the park where he would enjoy a walk around the park, rest at a bench and then continue his route back to the train station on his way home. His cover stops would be the diner, the train station and the park bench.
Agents of the resistance were sure to always have a cover. Cover is layered like an onion. It was literally life and death that they had a cover for action, a cover for status and a cover within a cover. In the case of our friend Jean; his first cover stop is the diner. Right time – right place, its morning, he’s going to breakfast. That’s his cover for action and cover for status. I’m going to the diner, its morning, I’m eating breakfast. Cover within a cover is a little bit harder to pull off. If a NAZI agent were to dig a little deeper “Jean” could say, “I’m a regular here. I eat breakfast here all the time three days a week. Just ask anyone.”
Assuming that “Jean” really is who he says he is, his cover within the cover should be fine. But what if his name really isn’t Jean? What if the Gestapo wanted to see papers? This is where good forgeries come in handy. There’s also something known as a back stop. So, let’s say Jean is really Carlo. Now German authorities wanted papers. So, he furnished them with some really good forgeries provided by support and auxiliary support cells. But they keep digging. Remember cover is established in layers. A back stop could be another member of the support who can vouch for him. A local employer, a fake parent. This is an apparatus that acts as a validating back stop under scrutiny. All these things have to be in place when running these sorts of operations.
UNDERGROUND PUBLICATIONS AND PROPAGANDA
Underground publications and leaflets were often handed out in the streets by the support cells. The materials would often be handed out and then passed around from person to person. It wasn’t a wise idea to be caught with the propaganda or publications in one’s house. This is exactly why they were passed from person to person in order to spread the word. Often code messages would be published or hidden in these materials directed specifically at various cryptonyms.
RADIO LONDRES
The free resistance were members of the resistance who had escaped France and made their way to London. It was from London that they would use the airwaves to communicate with guerrillas behind enemy lines and at the same time broadcast propaganda. This was not only a means of covert communication it was also a psychological operation launched against the enemy. They would change the frequency from which they were broadcasting and send messages in songs and poetry. Each night members of the insurgency would tune in and hear a message directed to specific groups or individuals. The message would be preceded by, “But First a message to our friends in France”.
The message would then be something that was completely out of context like, “Jean a une long moustache” (John has a long mustache). Radio Londres was instrumental in coordinating the resistance by calling them all to action hours in advance of the D-Day invasion. The message was set up days prior.
June 1st 1944 Radio Londres broadcast-ed a poem by Paul Verlaine via BBC. The poem “Chanson d’automne.” Was used. They only transmitted the first 3 lines, and it was to signify the invasion was to begin within the next 48 hours.
“Les sanglots longs
Des violons
De l’automne”
“When a sighing begins / In the violins / Of the autumn-song”
On June 5th another message was sent signifying the sabotage to begin. It was the next 3 lines.
“Blessent mon coeur
D’une langueur
Monotone”
“My heart wounded / The lack of energy (Melancholy )/ Languous (Lacking Spirit)”
These messages were the beginning of a united front by the insurgent resistance.
THE FRENCH RESISTANCE TODAY
One can only imagine how complex clandestine and covert communications could be had the NAZI occupation occurred in today’s era of modern high tech. Not only would the enemy have to be concerned with countering all of the fundamental trade craft of the past. They would also have to counter methods like using ghost email accounts for dead drop boxes, coded encrypted messages within JPEG files, Cell phone technology, GPS and GPS decoying and more. On the flip-side operatives would have to be extremely meticulous in choosing dead drop, hand-off and meeting sites. Cameras are everywhere to include private businesses, public areas and ATM machines.
Both the French and the Dutch Resistances were pivotal in changing history and tactics. They were instrumental in the allied success in Europe which of course is the reason we all do not speak German today. In addition their partnership with the OSS Jedburgh teams, SAS and MI6 led to amazing advancements and innovations in intelligence and other Special Operations. As a writer, lover of history and a former member of America’s Special Operations community, this is an amazing era to study.
Not only is it part of my lineage in the great brotherhood of unconventional warriors. It is the perfect case study of how techniques, tactics and procedures of unconventional warfare from previous generations were tested, utilized and expounded on during a great time of need. What their pioneering resulted in was the defeat of an evil tyrant and the freedom of an entire region. Their efforts maximized the force of minimal numbers and worked synergistic-ally with the overall effort to weaken and crush one of the most diabolical forces the world has ever seen. I wanted to share this information with those readers out there who like me cherish liberty and understand what it cost.
*The views and opinions expressed on this website are solely those of the original authors and contributors. These views and opinions do not necessarily represent those of Spotter Up Magazine, the administrative staff, and/or any/all contributors to this site.