“Unhappy it is though to reflect, that a Brother’s Sword has been sheathed in a Brother’s breast, and that, the once happy and peaceful plains of America are either to be drenched with Blood, or Inhabited by Slaves. Sad alternative! But can a virtuous Man hesitate in his choice?”
– George Washington
THE RIDE OF PAUL REVERE
In the early hours of 19 April 1775, Paul Revere, William Dawes and Samuel Prescott rode the night with the sole purpose of warning the Patriot Minuteman resistance of an impending force coming to the towns of Lexington and Concord. The British were crossing the Charles river and en route to Lexington and Concord for the purposes of arresting Samuel Adams and John Hancock. In addition to capturing key figures of the resistance they were also commissioned to confiscate any weapons and ammunition that the colonists had. Their targets were known militiamen homes, businesses and meeting places. There’s far more to the story than one might think though Henry Wadsworth Longfellow did a fantastic job of paraphrasing the epic with a poem.
Had Revere’s Ride, not been a success, Americans would likely still be part of the vast collection of British colonies across the globe. However, things could have gone far different if it weren’t for redundancy in planning and communications. Paul Revere had established an extensive covert and clandestine message and signaling system in his area of operation. Due to the escalation of resistance and violence against the British Imperial Occupying force by the Patriots, King George III implemented a series of oppressive legislation against the American colonists.
These key pieces of legislation which fell under the title of The Coercive Acts and Restraining Acts also known as the Intolerable Acts. They were designed to crush the will and spirit of the American people, to disable the resistance and quell any future rebellion before it could begin. These acts included:
The Administration of Justice Act – (20 May 1774) Also known as the Murder Act; Gave legal justification for Royal Authorities to act by any means necessary in order to prevent, quell or counter acts of dissent including protests and riots directed against the crown. The laws would prevent commanders and appointed figures of authority from receiving capital punishment
The Massachusetts Government Act – (20 May 1774) This legislation was commissioned to counter dissent and crush the resistance encountered by the Massachusetts government. It called for the removal of all publicly elected officials by the colonists and replaced the elected officials with a council of British loyalists and royal appointees. The Sheriff Identified and hand picked a list of jurors to be appointed to all trials and prohibited all town meetings. Town meetings were limited to once a year. This law was enacted to remove all legislative and electoral power from the people.
The Boston Port Act – (1 June 1774) As a result of the Boston Tea Party this piece of legislation effectually closed down the Boston Harbor to the people of Boston until they recognized the Tea Tax was in the justified Purview of the crown. In addition, the Boston Port Act required that the damages be paid to the East India Company for the tea that was lost. The port blockade was to be in place until “Bostonians proved that they were peaceable subjects” (I.E. The resistance was eradicated)
The Quartering Act – (2 June 1774) The original Quartering Acts of 1765 and 1766 required that British troops be allowed to stay at and be quartered in public facilities due to a shortage of barracks. The 1774 Act, included any residence within all the colonies, thus allowing the crown to have eyes and ears in any and every home they chose. In addition, this was meant to have a chilling effect on the populace and the resistance.
The result of the Coercive and Intolerable Acts were exactly the opposite of their intended purpose. This was foreseen by Edmond Burke and Lord Chatham who warned Massachusetts governor Sir Thomas Gage that this would in fact result in provocation and retaliation. The tightening of legislature and reprisals against Bostonians did nothing more than rally the other colonies to the aid of Boston. All of which led the colonists to escalate their activities and take things to the next progression in the development of the insurgency.
AMERICA AND THE WAY OF THE GUN
America was the land of the uncharted. It was wild, savage and free. Early colonists lived rugged lives. Most lived in the wilderness, ready to defend from creatures of the wild and mankind alike. Not only did colonists require firearms for food procurement and hunting, but defense from attacks by Native Americans and marauders. By 1775, the American Resistance was also in rapid development. Instances such as the 1770 Boston Massacre led to distrust and distain for the British. The massacre; a street brawl between colonists and a lone British soldier over taxation that turned into an all-out riot, the murder of 5 colonists and wounding of six; and an increased need for firearms. Colonists no longer trusted the British government at all and having firearms gave the sense of security that they might at least have a chance of protecting themselves from the occupying force.
When Thomas Gage called for increased restrictive and punitive legislation against the colonists under the Coercive Acts, he forbade town meetings and gatherings. Under once instance there was an illegal town meeting. Gage received word of this act of defiance and responded by sending red coat troops to break up the meeting. They were greeted by 3000 armed Americans. Gage’s Aide; John Andrews was noted for telling Gage that, “Anyone in the area 16 years or older owned a firearm and had gun powder.” Gage’s response was to call for the elimination of firearms and gun powder.
This retaliatory action by the British was enforced by ending all commerce that included firearms and gun powder from being transported or exchanged between Britain and the colonies. The Patriots of Lancaster County Pennsylvania released a statement, “That in the event of Great Britain attempting to force unjust laws upon us by the strength of arms; our cause we leave to heaven and our rifles.” At the same time a South Carolina Newspaper essay which was reprinted in Virginia also stated, “Any law that required the military to enforce it was necessarily legitimate.”
It was very clear to both the British and the Patriots that the key to American Liberty was by way of the gun. There were responses on both sides. The British response was to begin raiding American towns and confiscating firearms and powder. The colonist response was to begin smuggling, hiding and caching firearms and ammunition. September 1, 1774 Gage ordered a predawn raid with 260 Red Coats on Mystic River to seize several hundred barrels of powder from the Charleston Powder House. This became known as the “Powder Alarm”.
THE POWDER ALARM
The attack on the Charleston Powder House triggered the Worcester Convention. Townsmen gathered and ordered the resignations of all militia officers who received commissions from the royal governor. Soon after, Suffolk and Boston followed suit. Shortly after that the First Continental Congress assembled in Philadelphia Pennsylvania. There they urged all colonies to do the same. They then advocated sending supplies to the Bostonians.
Thomas Gage and King George III had made the mistake of attacking the one thing the colonists had left that provided them with means to food, security and the guarantee of liberty. The order was given to begin the execution of general warrantless searches with the objective being the confiscation of arms and ammunition. In October 1774, King George III began blocking the importation of all firearms and ammunition. Benjamin Franklin, then set out to import arms and ammunition from France, Spain and the Netherlands.
This led Paul Revere to travel to New Hampshire to warn of British ships that were approaching with the sole purpose of seizing cannons, firearms and ammunition. This information led to the raid on Fort William and Mary. December 14th 1774. 400 Patriots faced the British Army by conducting a raid on the arsenal at Fort William and Mary. They absconded with 100 barrels of ammunition. The very next day on 15 December, 1774; New Hampshire’s Friends of Liberty ran another assault on the arsenal. This time, they got away with stealing small arms, miscellaneous military supplies and 16 cannons stamped “Property of the king.” This was not the first raid conducted against the British crown. A successful raid had previously taken place in Rhode Island.
THE UNDERGROUND RESISTANCE
By Christmas 1774, the Patriot underground had clearly committed to the cause. With open acts of insurrection taking place across all the colonies, they were bracing for the inevitable. Firearms needed to be hidden in such a manner as to evade the warrantless searches by the Red Coats. This called for the development of a cache system. Safe houses had to be established to facilitate the movement and safety of members of the resistance. Covert and clandestine methods of communication had to be implemented in order to send communications between Patriot groups without compromise.
Because the British literally had eyes and ears everywhere, tradecraft from guerilla and operational cells had to be on point. From the ability to send secret communications, implement clandestine signals to guerrilla forces, cache, store, hide and disguise weapons and firearms and create plausible deniability for every action, the underground was fully activated.
CACHES
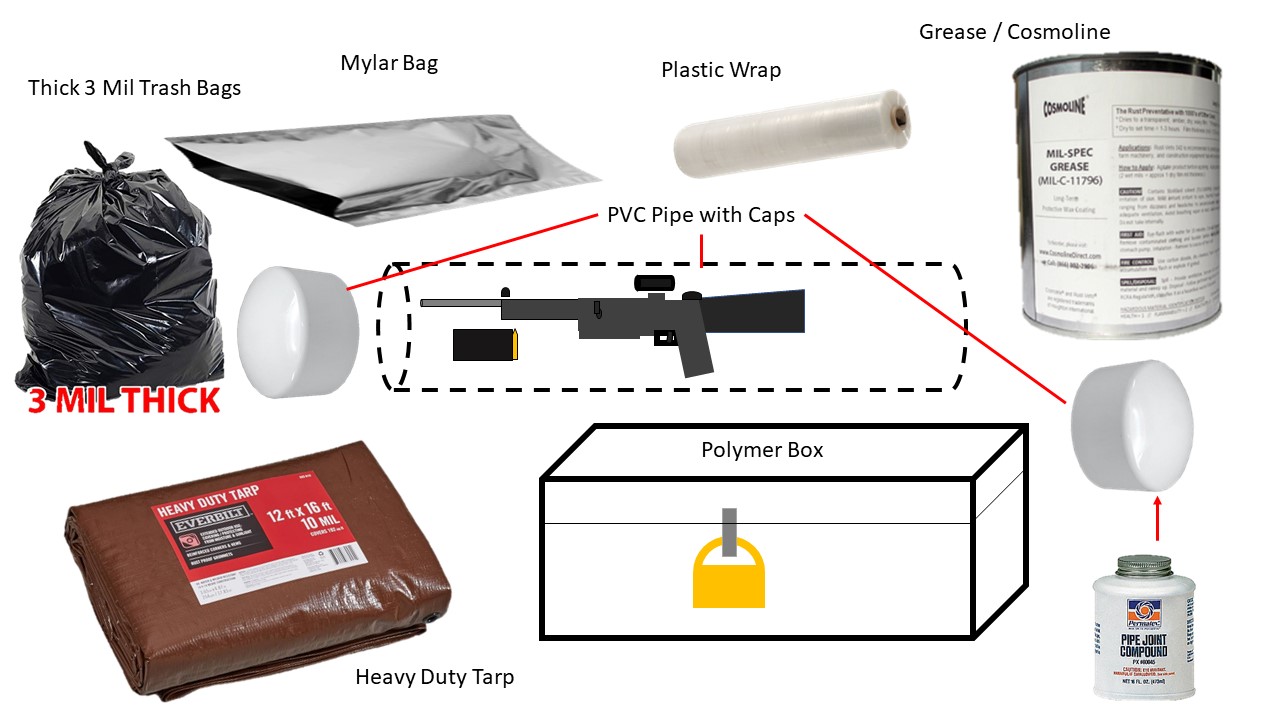
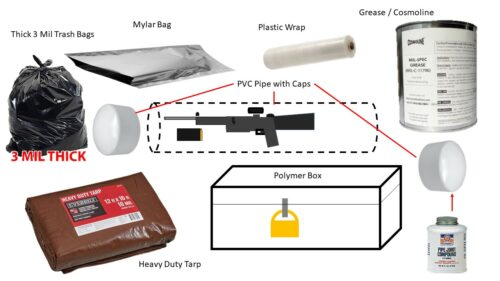
Caches are hidden storage places for supplies and equipment. When properly planned and established, caches permit irregular forces considerable freedom to operate throughout the Unconventional Warfare Operational Area, independent of their base areas. Caches reduce the amount of supplies Guerrilla elements must carry, thus enhancing foot mobility. Caches are located to support projected operations.
Caches can be implemented at various levels. In the instance of revolutionary patriots and militiamen, they may have weapons cached (hidden) even within the very walls or floorboards of their homes. In addition, they may have other small arms, cannons or powder; sealed, weatherproofed and buried in a nearby field or wood line. Caches may be for personal use or for use by a group.
When implementing a cache site into the plan; one must keep things simple.
A hidden, easy to identify location only by those within the group
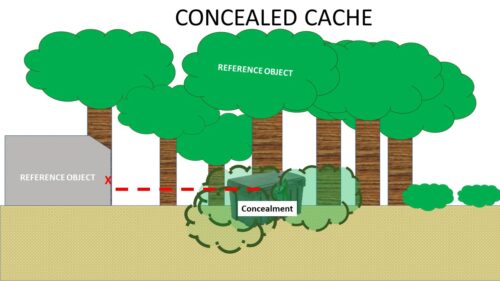
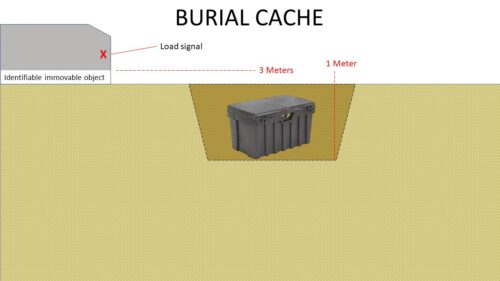
- The use of preferably natural or immovable manmade reference points I.E. (The old Oak tree at the North of the yard. Take 5 paces to the west of the oak tree. You will see a mossy boulder. The cache will be located approximately 1 meter to the north of the boulder. Buried 1 meter down.)
- Implementation of a load signal (If necessary) I.E. (The Boulder will be painted with a red “X” on the North face)
Hidden from plain sight
Hidden in such a manner as to evade an in-depth search from non-group member
May be time sensitive
May be evergreen – (Prolonged value)
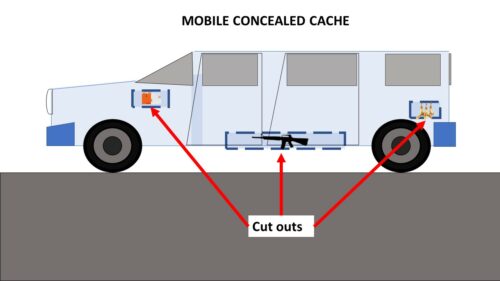
Caches may take several forms and be either internal or external. The example of an internal Cache is the hidden cache within the floorboards of a home. A cache that is hidden within the walls. There are also external caches such as the example given above and mobile caches. A mobile cache would be something as a horse carriage with hidden items stored within the chassis or frame of the vehicle. The last type of cache is a submersible cache. This type of cache would be waterproofed and placed below the line of sight under the water.
Internal Cache – Defined positioning based on an immovable piece of the structure. I.E. (The Master bedroom, approximately 3 meters south of the center of the northern wall. Look for the wooden plank on the floor with the “X” engraved on it)
External Cache – The use of preferably natural or immovable manmade reference points I.E. (The old Oak tree at the North of the yard. Take 5 paces to the west of the oak tree. You will see a mossy boulder. The cache will be located approximately 1 meter to the north of the boulder. Buried 1 meter down.)
Mobile Cache – This cache uses a moveable object such as a wagon or carriage that contains hidden contents
Concealed Cache – (See the examples above) Concealment requires the use of permanent man made or natural features to hide or disguises the cache. It has several advantages. Both employment and recovery usually and be done with minimum time and labour, and cached items concealed inside a building or dry cave are protected from the elements. Thus, they require less elaborate packaging. Also, in some cases, a concealed cache can be readily inspected from time to time to ensure that it is still usable. However, there is always the chance of accidental discovery in addition to all the hazards of wartime that may result in discovery or destruction or a concealed cache or denial of access to the site. The concealment method, therefore, is most suitable in cases where an exceptionally secure site is available or where a need for quick access to the cache justifies a calculated sacrifice in security.
Burial Cache – A cache that is buried below the ground
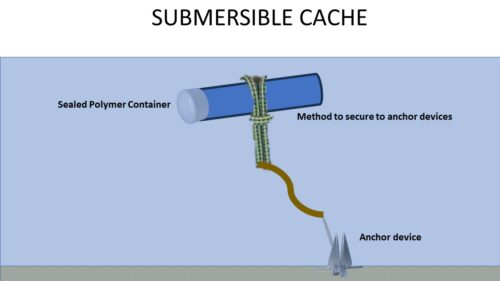
Submersible Cache – The submersible cache is either anchored beneath the surface of a body of water and buried or fixed into the earth below, or floating just below the surface, anchored to the earth below. It is unlikely that the Patriot resistance used submersible or floating caches in their operations due to the lack of weatherproofing technology of the day. Floating or submersible caches are the most difficult to emplace or retrieve.
There is very little available about the exact or precise methods of cache techniques employed by the early American resistance against the British other than the sheer mention of it. Much of the information presented in this article is speculative based on historical claims that the revolutionaries of the time, would hide and cache ammunition, weapons and equipment. The rest is based on this writer’s training and experience as a Special Forces Soldier, Infantry Scout and the Army Publications TC 31-29A, Special Forces Caching Techniques and FM 03-05.130 Army Special Operations Forces Unconventional Warfare.
Army Publication TC 31-29A, Special Forces Caching Techniques states:
“Caching is the process of hiding equipment or materials in a secure storage place with the view to future recovery for operational use. The ultimate success of caching may well depend upon attention to detail, that is, professional competence that may seem of minor importance to the untrained eye. Security factors, such as cover for the caching party, sterility of the items cached, and removal of even the slightest trace of the caching operations are vital. Highly important, too, are the technical factors that govern the preservation of the items in usable condition and the recording of data essential for recovery. Successful caching entails careful adherence to the basic principles of clandestine operations, as well as familiarity with the technicalities of caching.
Adequate burial sites can be found almost anywhere. Once in place, a properly buried cache is generally the best way of achieving lasting security. In contrast to concealment, however, burial in the ground is a laborious and time-consuming method of caching.
The disadvantages of burial are that:
Burial almost always requires a high-quality container or special wrapping to protect the Cache from moisture, chemicals and bacteria in the soil.
Emplacement or recovery of a buried cache usually takes so long that the operation must be done after dark unless the site is exceptionally secluded. It is especially difficult to identify and locate a buried cache.
Submersion sites that are suitable for secure concealment of a submerged cache are few and far between. Also, the container of a submerged cache must meet such high standards for waterproofing and resistance to external pressure that the use of field expedients is seldom workable. To ensure that a submerged cache remains dry and in place, planners must determine not only the depth of the water, but the type of bottom, the currents, and other facts that are relatively difficult for nonspecialists to obtain. Emplacement, likewise, requires a high degree of skill. At least two persons are needed for both emplacement and requires additional equipment. In view of the difficulties especially the difficulty of recovery the submersion method is suitable only on rare occasions. The most noteworthy usage is the relatively rare maritime resupply operation where it is impossible to deliver supplies directly to a reception committee. Caching supplies offshore by submersion is often preferable to sending a landing party ashore to bury a cache.”
THERE ARE 7 BASIC FACTORS WHEN IT COMES TO CACHE METHODS
- Purpose and Contents of the Cache
- Anticipated Enemy Action – In planning the caching operation, planners must consider the capabilities of any intelligence or security services not participating in the operation. They should also consider the potential hazards the enemy and its witting or unwitting accomplices present. If caching is done for wartime operational purposes, its ultimate success will depend largely on whether the planners anticipate the various obstacles to recovery, which the enemy and its accomplices will create if the enemy occupies the area. What are the possibilities that the enemy will preempt an ideal site for one reason or another and deny access to it? A vacant field surrounded by brush may seem ideal for a particular cache because it is near several highways. But such a location may also invite the enemy to locate an ordnance depot where the cache is buried
- Activities of the local Population – Probably more dangerous than deliberate enemy action are all of the chance circumstances that may result in the discovery of the cache. Normal activity, such as construction of a new building, may uncover the cache site or impede access to it. Bad luck cannot be anticipated, but it can probably be avoided by careful and imaginative observation of the prospective cache site and of the people who live near the site. If the cache is intended for wartime use, the planners must project how the residents will react to the pressures of war and conquest. For example, one of the more likely reactions is that many residents may resort to caching to avoid having their personal funds and valuables seized by the enemy. If caching becomes popular, any likely cache site will receive more than normal attention.
- Intended Actions by Allied Forces
- Packaging and Transportation Assets – Planners should assess the security needs and all of the potential obstacles and hazards that a prospective cache site can present. They should also consider whether the operational assets that could be used for packaging and transporting the package to the site. Best results are obtained when the packaging is done by experts at a packaging center The first question, therefore, is to decide whether the package can be transported from the headquarters or the field packaging center to the cache site securely and soon enough to meet the operational schedules. If not, the packaging must be done locally, perhaps in a safe house located within a few miles of the cache site. If such an arrangement is necessary, the choice of cache sites may be restricted by limited safe house possibilities.
- Personal Assets – All who participate directly in emplacement will know where the cache is located. Therefore, only the fewest possible and the most reliable persons should be used. Planners must consider the distance from the person’s residence to the prospective cache site and what action cover is required for the trip. Sometimes transportations and cover difficulties require the cache site to be within a limited distance of the person’s residence. The above considerations also apply to the recovery personnel.
- Caching Methods
LEXINGTON AND CONCORD
In the early hours of 19 April 1775, Paul Revere, William Dawes and Samuel Prescott rode the night with the sole purpose of warning the Patriot Minuteman resistance of an impending force coming to the towns of Lexington and Concord. The British were crossing the Charles river and en route to Lexington and Concord for the purposes of arresting Samuel Adams and John Hancock. In addition to capturing key figures of the resistance they were also commissioned to confiscate any weapons and ammunition that the colonists had. Their targets were known militiamen homes, businesses and meeting places.
Paul Revere had developed a very dynamic system of early warning, incorporating the use of signals and courier. Revere had foreseen the possibility that something may prohibit him from being able to leave Boston and deliver his message. It is for this reason he had built in redundancy in order to warn minutemen and other Patriot militia members. Not only did he plan on making his “midnight ride”, he had several back up couriers and the signal that would kick it all off was the lighting of two lanterns atop of Christ Church or the “Old North Church”.
Sexton Robert Newman and Vestryman Captain John Pulling Junior climbed to the top of the steeple and held two lanterns alerting the minutemen to make their way to the towns of Concord and Lexington. Revere made his way to Lexington within hours. Shortly after having arrived at Lexington Dawes arrived and they went about their way to Concord together. Along the way they had linked up with Samuel Prescott. Before making it to Concord the trio was stopped by a British patrol.
Paul Revere was taken into custody, Dawes lost his horse and escaped capture but was forced back to Lexington on foot. Samuel Prescott evaded capture and continued on to concord. It is said that Revere was held captive and underwent anywhere between one to two hours of interrogation when minuteman alarm shots were sounded, and he was then released while the Brits prepared for an impending clash with minutemen. Revere then continued on his way to concord.
Samuel Prescott made it to Concord by 2am. He promptly alerted the militiamen that British soldiers were on the march and by morning they would be at concord to find, confiscate or destroy any weapons or ammunition hidden by American Revolutionists. Shortly after Revere arrived and notified the militiamen that the British were already embattled just outside of Lexington. Had it not been for the clash with the minutemen Revere might not have made it to Concord at all. Shortly after arriving in Concord the Patriots and their minuteman militia made their way to the North Bridge. There at the North Bridge Colonel James Barrett would discuss plans to counter the Red Coat forces set to march on Concord.
When the British force arrived in Concord early on the morning of 19 April 1775, their first stop was at the home of Colonel Barrett. Barrett was the local militia leader and it was thought that if in fact there were to be weapons and ammunition or people of interests such as Adams and Hancock to be found; it would be at his home. The colonel had left a few hours prior and the Red Coat commander was met by the woman of the house. They demanded breakfast for the troops. Reluctantly the lady of the house fed them as required.
During the visit to the Barret home the lady was interrogated as to the whereabouts of the man of the house and location of any weapons, ammunition or people of interest. What they didn’t know is that the previous day Colonel Barrett had his sons plow the fields and in doing so they cached weapons in crops. The British marched by the buried weapons. This is very similar to how Taliban, HIG and Al-Qeida will bury and cache weapons and munitions in the confines of their orchards in Afghanistan today.
Upon leaving the Barrett home and making their way to search the rest of the village Mrs. Barrett had complained that the British had come to her home, ate her food and then refused to pay for it. At which point one of the officers offered her a few shillings. To her reply, “This was the price of blood.”
The second planned stop was the Ephraim Jones Tavern. It was a rumored weapons depot for Patriots. During their search they discovered weapons and cannons. It was at this point the soldiers ban to set fires. They then began towards the homes of locals. It was at this point the locals were able to convince the soldiers to actually put out the fires. The soldiers had developed a certain respect for the locals who had quartered and fed them in the past. It was this relationship that allowed the locals to convince the soldiers to put out the fires they had already set and to lead them away from the rest of the hidden weapons and ammunition caches. This also bought more time for the gathering minutemen to prepare for battle at the North Bridge.
After leaving Concord the Red Coats marched on toward the North Bridge, where the minutemen had been gathering and preparing for battle. It was at the North Bridge where 800 British troops met against 400 Patriot militia. The British commander called for the minutemen to lay down their arms. This call was met by Patriot fire. The British were caught off guard. They were only presented with a portion of the minutemen on the ground. A portion of the Patriots were at the bridge and the rest were concealed behind cover all around the British force.
The Patriots used a strike and run style of battle employing cover and concealment. This made it difficult for the Red Coats to identify where the threat was coming from. The result of the Patriot guerrilla tactics were 300 wounded Red Coats and 73 killed. The minutemen pursued the British all the way back to Boston. The militia would alternate between fighting troops online and then attacking the retreating troops. All the while, minute men continued pouring in and running back and forth between hidden weapons and ammunition caches and the battle.
The Red Coats were so overwhelmed that they began lighting homes on fire and shooting anyone thought to be a “sniper” out of desperation and paranoia. These desperate acts set up the Patriots for justification at the Battle of Boston later on. The British condemned the Patriots for “Ungentlemanly Combat” tactics. Overall the battles of Lexington and Concord were a great success for the revolutionaries and were then considered the defining acts for which the Revolutionary war began.
THE VIRTUOUS DECISION
George Washington had gotten wind of the victories at Lexington and Concord. He drafted the following response in a letter addressed to George William Fairfax. Fairfax was a close friend of Washington. The letter discussed the events of Lexington and Concord. Excerpts from the letter are as follows:
“General Gage acknowledges, that the detachment under Lieutenant Colonel Smith was sent out to destroy private property; or, in other Words, to destroy a Magazine which self preservation obliged the Inhabitants to establish. And he also confesses, in effect at least, that his Men made a very precipitate retreat from Concord, notwithstanding the reinforcement under Lord Piercy, the last of which may serve to convince Lord Sandwich (and others of the same sentiment) that the Americans will fight for their Liberties and property, however pusilanimous, in his Lordship’s Eye, they may appear in other respects.”
Washington acknowledged the fact that Gage had sent men to Lexington and Concord for the sole purpose of either destroying or taking weapons that citizens depended on for “Self Preservation”. The letter goes on:
“Unhappy it is though to reflect, that a Brother’s Sword has been sheathed in a Brother’s breast, and that, the once happy and peaceful plains of America are either to be drenched with Blood, or Inhabited by Slaves. Sad alternative! But can a virtuous Man hesitate in his choice?”
And here we can clearly see Washington had come to the realization that any government who would attempt to take away one’s ability to protect one’s self would readily enforce slavery amongst the populous and therefore only bloodshed could prevent such a fate. In which case he believed resistance through force as the virtuous choice.
ARE YOU VIRTUOUS?
Make no mistake the American colonists were able to stomach a great deal of treachery from their government and their King. It was at the point that the government attempted to confiscate the firearms of the colonists that they took a hard stand. It was the restriction and the confiscation of guns that triggered the American Revolution. This was the very reason for the battle of Lexington and Concord. Furthermore, this took place because in an attempt by the government to quell a gathering the Patriots stood up to the British with 3000 armed men. Therefore, the King realized so long as the society is armed they have the ability to resist the will and tyranny of the King.
Recently mass shootings have fueled the communist insurgency within the United States to call for the implementation and enforcement of laws to the degree of the “intolerable acts”. These proposed laws would in fact have a chilling effect on the population. It would make into law the perception that someone is a threat and therefore is stripped of their due process and second amendment right. It is no coincidence that the FBI recently released a report stating that criticism of the government and political ideologies can be considered a “conspiracy theory” and was considered dangerous.
The FBI report can be seen as a compliment or annex to the DHS Rightwing Extremism report published April 7th 2009. The DHS report states that Constitutionalists, those of Fiscal Conservativism philosophies, Christians and returning Combat Veterans are aligned with White Supremacists and other Rightwing Extremists. So these new laws would essentially establish a social credit score for each individual and anyone “flagged” under the FBI or DHS definition of extremism would be denied their right to bear arms.
This would happen on several levels. First if you don’t already have a firearm and are “flagged” and attempt to purchase one, you will be denied. You may not even know that you are flagged until you attempt to buy. Thus the expansion of the already established, “no buy list” Secondly, if you are suspected of having firearms and are on the “Red flag” list you will have your firearms confiscated and then you must pursue your due process to justify your innocence. Then there is yet a third option. The third possibility would be that you have firearms and are “Red Flagged”, at which point you are subpoenaed to court to prove your innocence of a crime that has not yet been committed.
All of these are reasons for insurrection. All of these are restrictions that our ancestors would not have tolerated. These “Red Flag” Laws, are the very reason we have a Bill of rights. These proposed laws have already resulted in the murder of one man in Maryland, who refused to surrender his arms and cede his constitutional rights. These laws will be used to silence and suppress anyone who would dare question the shadow government.
The acceptance of such laws would delegitimize the Constitution and Bill of Rights our ancestors fought, killed and died for. To accept such legislation is a work around of the right to free speech, the right to bear arms, the right to due process and the protection against warrantless searches. Perhaps its time that we take a lesson from our own history.
*The views and opinions expressed on this website are solely those of the original authors and contributors. These views and opinions do not necessarily represent those of Spotter Up Magazine, the administrative staff, and/or any/all contributors to this site.